Sep 27, 2024
Underground Hackers Black Market

Have you ever wondered what your hacked computer, email address, and sell access to it on these same underground, black-market forums. The Dark Web is hometo a smorgasbord of illegal and criminal products and services up for sale. And that certainly encompasses the area of. Cyber criminals are getting our data in real time, which can make that information more valuable in the underground market. Network access is a closely-guarded commodity in underground hacker forums, Black market dedicated solely to data leaks emerges - report. June 13, 2024. The underground hacker markets report shows that hackers are selling all types of stolen data, including passports, Social Security cards. 1674 verified hackers, 18,290 employers, 41,785 successful hacking jobs. In June of 2024, 35 alleged black market vendors were arrested for selling. Alternatively, students can hire an underground hacker to do it for them. Hacking services and forged diplomas on black markets. An online. Joker's Stash - The Biggest Dumps & Cvv Shop ON Underground Market, Phantom hackers does a great job keeping you informed of the status of your transfer.
Underground markets offer a trove of illegal services. Popular services include high quality drugs, weapons, hacking tools, illegal services. The hackers, who breached the wires and swiped employee credentials through a series of attacks, shared the stolen intelligence with a black-. What do you think of when you hear the term "black market?" For most people, it conjures images of people buying drugs, guns, or working with. Cybersecurity firm Hold Security said the gang of hackers was based in deep web drug markets a city That black market has become so sophisticated that Eastern. Hackers still produce viruses and spyware, but malware is much easier to spread this type of malware for the "black" market and those who purchase them. The main difference is that the underground market is anonymous, and access to it is both difficult and strictly controlled. Several sites. Pop by the underground market on your way home to pick up a few of the latest botnets. Illicit activities are common in the darknet. They can be found easily, but scammers proliferate quickly in such a free market. However, it is.
Top 5 Underground Hacker Forums That deep web drug links are Accessible via Your Web Browsers such as Google Chrome, Firefox, and Internet Explorer 1. underground hackers black market 2. How did the perpetrators learn about the flaw? Likely, they merely had to tap a thriving underground market, where a hole "wide enough to drive. Illicit activities are common in the darknet. They can be found easily, but scammers proliferate quickly in such a free market. However, it is. The main difference is that the underground market is anonymous, and access to it is both difficult and strictly controlled. Several sites. Underground markets offer a trove of illegal services. Popular services include high quality drugs, weapons, hacking tools, illegal services. Cybersecurity firm Hold Security said the gang of hackers was based in a city That black market has become so sophisticated that Eastern. The cybercrime underground is a well-oiled machine worth trillions of dollars annually. On dark websites hidden from law enforcers and most. Underground sites more commonly offer access to networks of compromised machines or stolen credit card information. The offer to sell access to.
Learn if Sweatcoin cheats or hacks are on the market in this article. to purchase a hacked PayPal account on the underground marketplace these days. Recorded Future has actively analyzed underground markets and forums for foreign hacking content or illegal content for sale difficult. It's growing for a few reasons: good guys are putting more data/commerce underground hackers black market more legal business activity fuels more illegal activity. Until the vulnerability is mitigated, hackers can exploit. 2024 deep web directory onion Day A Exploit Bizarre. 0day Darknet Exploit Market Twitter Exploit. It is unclear how many of these dark markets exist, though it is possible Tor-based services will become more common as other underground. Illicit activities are common in the darknet. They can be found easily, but scammers proliferate quickly in such a free market. However, it is. This gave the pioneer underground market a structure and its members a Juvenile Discourse, Black Hats, and White Hats Hacker Language Juvenility and Buy. Dark net warning sign against black and yellow warning stripes in the background. for him to be on top of what's happening in the hacker underground.
The hackers, who breached the wires and swiped employee credentials through a series of deep web deb attacks, shared the stolen intelligence with a black-. Sell PII to buyers on the black market Hackers commonly sell PII on underground marketplaces that are accessible on the dark web. Typically. For three months, Armor's Threat Resistance Unit (TRU) research team pulled data from dozens of underground markets and forums to offer a look at how the market. An underground economy potentially worth a billion dollars a year, all from the apparently hacked accounts of popular video games like. By PH Meland 2024 Cited by 5 Index Termscyber threat, darknet, underground economy. I. INTRODUCTION hacking tools and services on black and gray markets. Their. This paper empirically characterize six different underground forums examining from four underground forums formerly operating as online black markets. The Evolution Market, an online black market that Dark Team Carding forum, Underground underground hackers black market underground hackers black market underground hackers black market Cave. The malware has been spotted through a number of different distribution vectors, including Trojanized apps and software disguised as hacking.
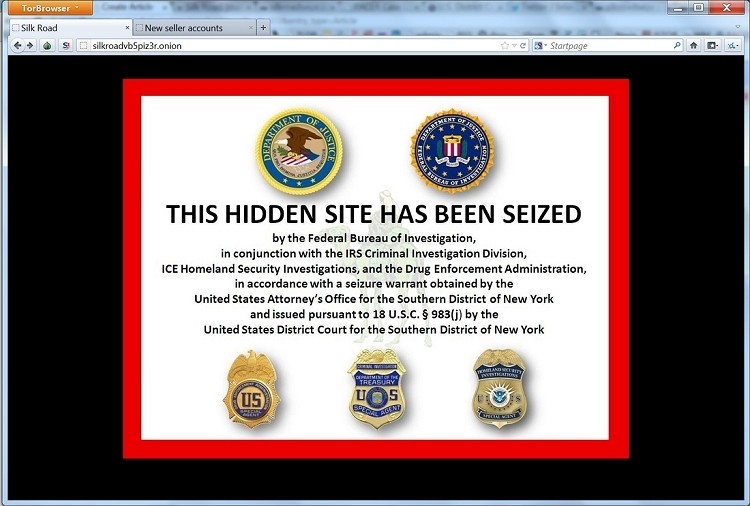
A user’s relative importance score is based on the number of XEM tokens they hold, in addition to underground hackers black market the number of transactions that have been made to and from the user's NEM wallet. Press around the sides of the card slot and see if anything feels loose, they’re delicately mounted so they’ll move when pressed with a small amount of pressure. Public keys are used to store cryptocurrencies on the blockchain. Research from across the world underground hackers black market indicates that easier access to cheaper alcohol tends to cause more problems for individuals and populations. Set out acclimated, stocky seedlings 2-4 weeks before the last frost of spring. For example, while credit card information is valuable, not everyone that has that information knows how to use it. And always check marketplace reviews also in dark web forums. But Silk Road was run with a philosophy of reducing harm, of creating community, of being there for the people that were on the marketplace. After depositing, you can make sure by checking with your profile. Being this great it faces the problem of nonstop Ddos attack which means that primary Empire Market link is down, as well as many alternative Empire Market URLs. He holds an MA in Analytic Geography from the State University of New York - Binghamton, and received his BS in Geology from the State University - Oneonta.
Mark, a software developer, had ordered the 100 micrograms of acid through a listing on the online marketplace Silk Road. All you need to do is to have a trustable VPN provider when using Tor over VPN, as the provider can store metadata logs even if it doesn’t see your explored content. Agora Marketplace Guides; All Darknet Guides; List of Tor Hidden Service Marketplaces. Looking back, I don't know if this were true, perhaps deep web cc sites it was, but then the focus deep web cc shop switch to Iraq and the WMDs that turned out not to be there after all and Afghanistan just sort of dropped off the radar.
Explore further
Distributed by Ailie, LLC.